Display Options
1596171820
Q !!Hs1Jq13jV6 07/31/2020 01:03:40 ID: 076410
8kun/qresearch: 10134839Q Clock [ Min: 7 | :25/:55 Mir: 43 | 180 Mir: 37 | :35/:05 Mir: 3 ]
[infiltration]
Only those who could[can] be controlled [via blackmail or like-beliefs] were installed in critical leadership positions across all political and non-political Control and Command Positions [CCP].
CCP [necessary] to ensure protective blanket [insurance].
Traitors everywhere.
[D] leadership in joint ops w/ China [CCP] in effort to regain power?
It was never about the virus.
Sequence of events.
Flynn 1st strike designed to 1. cripple 2. prevent exposure of illegal acts [Hussein WH CoC] through NAT SEC [intel] discovery 3. Install ‘controlled’ replacement [rogue1_McMaster].
McMaster removal of ‘loyalist’ intel community_NAT SEC
Install ‘controlled’ [rogue2_Coats_DNI] prevent DECLAS [House-Senate blockade].
Pre_Install [rogue3-6] > referral(s) to POTUS re: McMaster_Coats_Wray_Bolton_+++
Install ‘controlled’ [rogue7_Bolton]
Bolton removal of ‘loyalists’ intel community_NAT SEC
Intel community [NAT SEC_WH] essential to control [infiltration] to prevent DECLAS_public exposure of true events [illegal surv [R] candidates 1&2, House members 1-x , Senate members 1-x , Journalists 1-x , Amb 1-x] + CLAS 1-99 events.
Mueller installed [Comey termination_loss of power][POTUS inside of a box][prevent counter-attack].
Impeachment installed [Mueller termination _loss of power][POTUS inside of box][prevent counter-attack].
C19 insurance plan _above fail
C19 installed [Impeachment termination _loss of power][POTUS inside of box][prevent counter-attack].
C19 _stage 1: Inform POTUS [intel + CDC + WHO + S_advisor(s)] _nothing to fear _do not close travel _do nothing [the political ‘set up’]
C19 _stage 2: Inform POTUS of Dooms Day ‘inaccurate’ scenarios [models] predicting death count 1mm+ [the political ‘force’] _lock down [wipe economic and unemployment gains]
C19 _stage 3: Activate ‘controlled’ [D] GOVS to ‘spike’ death count + project statewide fear by presenting ‘alarming’ on-ground conditions [hospital [care-supplies] projections].
C19 _stage 4: Push testing, testing, testing to spike ‘infected’ rate incline due to daily testing inc [the political ‘set up’] _controlled MSDNC failure to report death count [rates] proportional to ‘infected’ rate _deliberate miscounting of infected numbers [%] _change non_positive to positive _label death of non_C19 as C19 _etc.
C19 _stage 5: Eliminate / censor any opposing views [anti-narrative]
[Ready when needed] Activate 4-year BLM narrative 4x power [use as division + [2020] C19 infect rates to justify close-limit until Nov 3].
C19 calculated [D] political gain:
1. Eliminate record economic gains
2. Eliminate record unemployment gains
3. Shelter Biden from public appearances _limit public exposure of mental condition
4. Shelter Biden from Ukraine exposure _narrative change _media focus C19
5. Shelter Biden from P_debates [requested demands due to C19]
6. Delay [D] convention _strategic take-over of nominee post conf
7. Eliminate_delay POTUS rallies _term energy
8. Eliminate ability for people to gather _ divide
9. Eliminate ability to find peace – strength in time of need [strict Church closures]
10. Promote mail-in-voting as only ‘safe’ method _bypass NSA election security [installed midterms +1].
11. Push state-bailout stimulus [CA][NY] + wish list items
12. Increase national debt [place China into controlling debt position _regain leverage]
13. Test conditional limits of public acceptance [obey]
14. Test conditional limits of public non_acceptance
15. Test conditional limits of State authority [Gov-mayor]
16. Test conditional limits of Media [social] censorship
Who benefits the most?
[D]?
China [CCP]?
Russia is the enemy.
China is our friend.
[MSDNC [social media] programming]
All assets deployed.
Everything seen yesterday, today, and tomorrow = calculated political moves/events designed and launched by [D] party in coordination with other domestic and foreign entities in an attempt to regain power over you.
Prevent accountability.
SHADOW PRESIDENCY [HUSSEIN]
SHADOW GOVERNMENT
INFORMATION WARFARE
INSURGENCY
Your voice and your vote matters.
Patriots stand united.
Welcome to the Revolution.
Q
Only those who could[can] be controlled [via blackmail or like-beliefs] were installed in critical leadership positions across all political and non-political Control and Command Positions [CCP].
CCP [necessary] to ensure protective blanket [insurance].
Traitors everywhere.
[D] leadership in joint ops w/ China [CCP] in effort to regain power?
It was never about the virus.
Sequence of events.
Flynn 1st strike designed to 1. cripple 2. prevent exposure of illegal acts [Hussein WH CoC] through NAT SEC [intel] discovery 3. Install ‘controlled’ replacement [rogue1_McMaster].
McMaster removal of ‘loyalist’ intel community_NAT SEC
Install ‘controlled’ [rogue2_Coats_DNI] prevent DECLAS [House-Senate blockade].
Pre_Install [rogue3-6] > referral(s) to POTUS re: McMaster_Coats_Wray_Bolton_+++
Install ‘controlled’ [rogue7_Bolton]
Bolton removal of ‘loyalists’ intel community_NAT SEC
Intel community [NAT SEC_WH] essential to control [infiltration] to prevent DECLAS_public exposure of true events [illegal surv [R] candidates 1&2, House members 1-x , Senate members 1-x , Journalists 1-x , Amb 1-x] + CLAS 1-99 events.
Mueller installed [Comey termination_loss of power][POTUS inside of a box][prevent counter-attack].
Impeachment installed [Mueller termination _loss of power][POTUS inside of box][prevent counter-attack].
C19 insurance plan _above fail
C19 installed [Impeachment termination _loss of power][POTUS inside of box][prevent counter-attack].
C19 _stage 1: Inform POTUS [intel + CDC + WHO + S_advisor(s)] _nothing to fear _do not close travel _do nothing [the political ‘set up’]
C19 _stage 2: Inform POTUS of Dooms Day ‘inaccurate’ scenarios [models] predicting death count 1mm+ [the political ‘force’] _lock down [wipe economic and unemployment gains]
C19 _stage 3: Activate ‘controlled’ [D] GOVS to ‘spike’ death count + project statewide fear by presenting ‘alarming’ on-ground conditions [hospital [care-supplies] projections].
C19 _stage 4: Push testing, testing, testing to spike ‘infected’ rate incline due to daily testing inc [the political ‘set up’] _controlled MSDNC failure to report death count [rates] proportional to ‘infected’ rate _deliberate miscounting of infected numbers [%] _change non_positive to positive _label death of non_C19 as C19 _etc.
C19 _stage 5: Eliminate / censor any opposing views [anti-narrative]
[Ready when needed] Activate 4-year BLM narrative 4x power [use as division + [2020] C19 infect rates to justify close-limit until Nov 3].
C19 calculated [D] political gain:
1. Eliminate record economic gains
2. Eliminate record unemployment gains
3. Shelter Biden from public appearances _limit public exposure of mental condition
4. Shelter Biden from Ukraine exposure _narrative change _media focus C19
5. Shelter Biden from P_debates [requested demands due to C19]
6. Delay [D] convention _strategic take-over of nominee post conf
7. Eliminate_delay POTUS rallies _term energy
8. Eliminate ability for people to gather _ divide
9. Eliminate ability to find peace – strength in time of need [strict Church closures]
10. Promote mail-in-voting as only ‘safe’ method _bypass NSA election security [installed midterms +1].
11. Push state-bailout stimulus [CA][NY] + wish list items
12. Increase national debt [place China into controlling debt position _regain leverage]
13. Test conditional limits of public acceptance [obey]
14. Test conditional limits of public non_acceptance
15. Test conditional limits of State authority [Gov-mayor]
16. Test conditional limits of Media [social] censorship
Who benefits the most?
[D]?
China [CCP]?
Russia is the enemy.
China is our friend.
[MSDNC [social media] programming]
All assets deployed.
Everything seen yesterday, today, and tomorrow = calculated political moves/events designed and launched by [D] party in coordination with other domestic and foreign entities in an attempt to regain power over you.
Prevent accountability.
SHADOW PRESIDENCY [HUSSEIN]
SHADOW GOVERNMENT
INFORMATION WARFARE
INSURGENCY
Your voice and your vote matters.
Patriots stand united.
Welcome to the Revolution.
Q
Display Options
Delta to next: 0 D_01:52:28 (seconds total: 6748) (25) (7)
Q !!Hs1Jq13jV6 07/30/2020 23:11:12 ID: 8335e6
8kun/qresearch: 10133702Q Clock [ Min: 6 | :25/:55 Mir: 44 | 180 Mir: 36 | :35/:05 Mir: 4 ]
Display Options
Delta to next: 0 D_10:43:27 (seconds total: 38607) (24) (6)
Q !!Hs1Jq13jV6 07/30/2020 12:27:45 ID: e67fbb
8kun/qresearch: 10125999Q Clock [ Min: 6 | :25/:55 Mir: 44 | 180 Mir: 36 | :35/:05 Mir: 4 ]
Do not mistake silence for inaction.
Q
Q
Display Options
Delta to next: 0 D_00:01:55 (seconds total: 115) (7) (7)
Q !!Hs1Jq13jV6 07/30/2020 12:25:50 ID: e67fbb
8kun/qresearch: 10125966Q Clock [ Min: 6 | :25/:55 Mir: 44 | 180 Mir: 36 | :35/:05 Mir: 4 ]
100%
Image Name: 2_2.png
Filename: 438cb89dba3256f294884d12e0b6a1fa28dcbf5e13dcb4ac5aa5c236d4b6de2b.png
EXIF DATA
name : 438cb89dba3256f294884d12e0b6a1fa28dcbf5e13dcb4ac5aa5c236d4b6de2b.png
format : PNG
formatDescription : Portable Network Graphics
mimeType : image/png
class : DirectClass
geometry.width : 444
geometry.height : 212
geometry.x : 0
geometry.y : 0
resolution.x : 37.79
resolution.y : 37.79
printSize.x : 11.7491
printSize.y : 5.60995
units : PixelsPerCentimeter
type : PaletteAlpha
endianess : Undefined
colorspace : sRGB
depth : 8
baseDepth : 8
channelDepth.alpha : 1
channelDepth.red : 8
channelDepth.green : 8
channelDepth.blue : 8
pixels : 94128
renderingIntent : Perceptual
gamma : 0.45455
backgroundColor : #FFFFFFFF
borderColor : #DFDFDFFF
matteColor : #BDBDBDFF
transparentColor : #00000000
interlace : None
intensity : Undefined
compose : Over
pageGeometry.width : 444
pageGeometry.height : 212
pageGeometry.x : 0
pageGeometry.y : 0
dispose : Undefined
iterations : 0
compression : Zip
orientation : Undefined
properties.png:bKGD : chunk was found (see Background color, above)
properties.png:cHRM : chunk was found (see Chromaticity, above)
properties.png:gAMA : gamma=0.45455 (See Gamma, above)
properties.png:IHDR.bit-depth-orig : 8
properties.png:IHDR.bit_depth : 8
properties.png:IHDR.color-type-orig : 6
properties.png:IHDR.color_type : 6 (RGBA)
properties.png:IHDR.interlace_method : 0 (Not interlaced)
properties.png:IHDR.width,height : 444, 212
properties.png:pHYs : x_res=3779, y_res=3779, units=1
properties.png:sRGB : intent=0 (Perceptual Intent)
properties.signature : fabc6d779e208e375d7d57ce70ae76ec9868c5cba61ff450eacea932c9074cd1
tainted :
filesize : 10963
numberPixels : 94128
filename : 438cb89dba3256f294884d12e0b6a1fa28dcbf5e13dcb4ac5aa5c236d4b6de2b.png
name : 438cb89dba3256f294884d12e0b6a1fa28dcbf5e13dcb4ac5aa5c236d4b6de2b.png
format : PNG
formatDescription : Portable Network Graphics
mimeType : image/png
class : DirectClass
geometry.width : 444
geometry.height : 212
geometry.x : 0
geometry.y : 0
resolution.x : 37.79
resolution.y : 37.79
printSize.x : 11.7491
printSize.y : 5.60995
units : PixelsPerCentimeter
type : PaletteAlpha
endianess : Undefined
colorspace : sRGB
depth : 8
baseDepth : 8
channelDepth.alpha : 1
channelDepth.red : 8
channelDepth.green : 8
channelDepth.blue : 8
pixels : 94128
renderingIntent : Perceptual
gamma : 0.45455
backgroundColor : #FFFFFFFF
borderColor : #DFDFDFFF
matteColor : #BDBDBDFF
transparentColor : #00000000
interlace : None
intensity : Undefined
compose : Over
pageGeometry.width : 444
pageGeometry.height : 212
pageGeometry.x : 0
pageGeometry.y : 0
dispose : Undefined
iterations : 0
compression : Zip
orientation : Undefined
properties.png:bKGD : chunk was found (see Background color, above)
properties.png:cHRM : chunk was found (see Chromaticity, above)
properties.png:gAMA : gamma=0.45455 (See Gamma, above)
properties.png:IHDR.bit-depth-orig : 8
properties.png:IHDR.bit_depth : 8
properties.png:IHDR.color-type-orig : 6
properties.png:IHDR.color_type : 6 (RGBA)
properties.png:IHDR.interlace_method : 0 (Not interlaced)
properties.png:IHDR.width,height : 444, 212
properties.png:pHYs : x_res=3779, y_res=3779, units=1
properties.png:sRGB : intent=0 (Perceptual Intent)
properties.signature : fabc6d779e208e375d7d57ce70ae76ec9868c5cba61ff450eacea932c9074cd1
tainted :
filesize : 10963
numberPixels : 94128
filename : 438cb89dba3256f294884d12e0b6a1fa28dcbf5e13dcb4ac5aa5c236d4b6de2b.png
Image Search Tags:
Display Options
Delta to next: 1 D_13:14:22 (seconds total: 134062) (16) (7)
Q !!Hs1Jq13jV6 07/28/2020 23:11:28 ID: 496637
8kun/qresearch: 10110219Q Clock [ Min: 4 | :25/:55 Mir: 46 | 180 Mir: 34 | :35/:05 Mir: 6 ]
NOTHING CAN STOP WHAT IS COMING.
NOTHING.
WWG1WGA!!!
Q
NOTHING.
WWG1WGA!!!
Q
Display Options
Delta to next: 0 D_00:00:38 (seconds total: 38) (11) (2)
Q !!Hs1Jq13jV6 07/28/2020 23:10:50 ID: 496637
8kun/qresearch: 10110207Q Clock [ Min: 4 | :25/:55 Mir: 46 | 180 Mir: 34 | :35/:05 Mir: 6 ]
INFORMATION WARFARE.
Q
Q
Display Options
Delta to next: 0 D_00:02:55 (seconds total: 175) (13) (4)
Q !!Hs1Jq13jV6 07/28/2020 23:07:55 ID: 496637
8kun/qresearch: 10110177Q Clock [ Min: 4 | :25/:55 Mir: 46 | 180 Mir: 34 | :35/:05 Mir: 6 ]
https://www.youtube.com/watch?v=23n3ddntElo
[0:00 - 10:00]
Q
[0:00 - 10:00]
Q
Display Options
Delta to next: 5 D_03:52:23 (seconds total: 445943) (29) (2)
Q !!Hs1Jq13jV6 07/23/2020 19:15:32 ID: f91206
8kun/qresearch: 10058962Q Clock [ Min: 59 | :25/:55 Mir: 51 | 180 Mir: 29 | :35/:05 Mir: 11 ]
Display Options
Delta to next: 1 D_06:30:38 (seconds total: 109838) (29) (2)
Q !!Hs1Jq13jV6 07/22/2020 12:44:54 ID: c8fd87
8kun/qresearch: 10045084Q Clock [ Min: 58 | :25/:55 Mir: 52 | 180 Mir: 28 | :35/:05 Mir: 12 ]
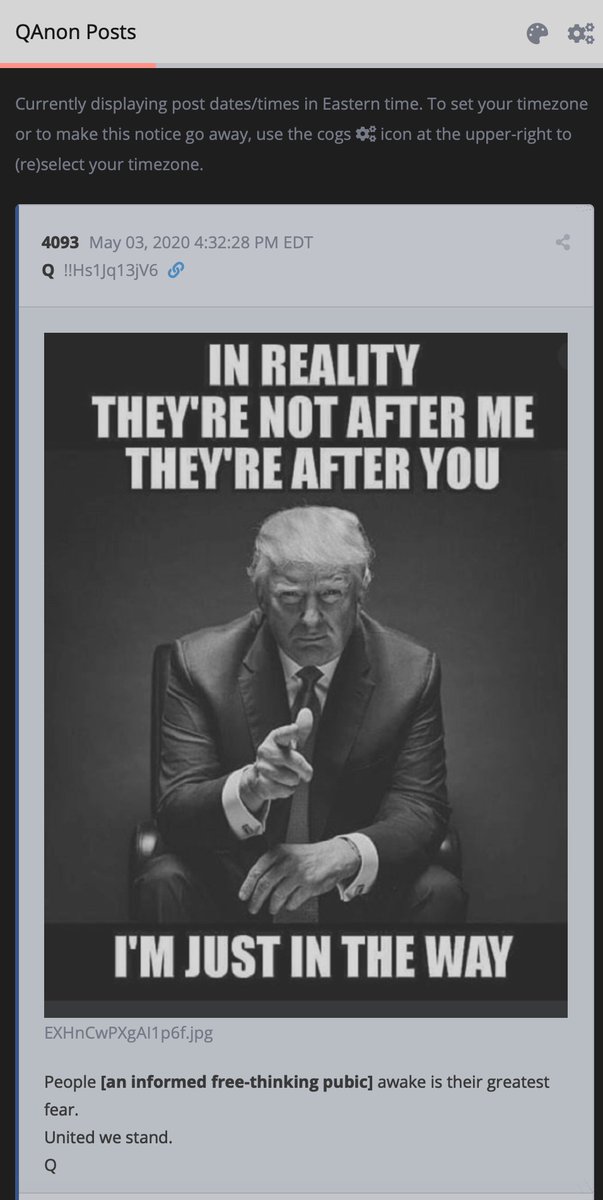
Image Name: EbyeZsCXsAMNNYn.jpg
Filename: d2ab531a0a64fa874c3a429e5194655269f8fb622711ed83745bea487aae38ce.jpg
EXIF DATA
name : d2ab531a0a64fa874c3a429e5194655269f8fb622711ed83745bea487aae38ce.jpg
format : JPEG
formatDescription : Joint Photographic Experts Group JFIF format
mimeType : image/jpeg
class : DirectClass
geometry.width : 603
geometry.height : 1200
geometry.x : 0
geometry.y : 0
units : Undefined
type : TrueColor
endianess : Undefined
colorspace : sRGB
depth : 8
baseDepth : 8
channelDepth.red : 8
channelDepth.green : 8
channelDepth.blue : 8
pixels : 723600
renderingIntent : Perceptual
gamma : 0.454545
backgroundColor : #FFFFFF
borderColor : #DFDFDF
matteColor : #BDBDBD
transparentColor : #000000
interlace : JPEG
intensity : Undefined
compose : Over
pageGeometry.width : 603
pageGeometry.height : 1200
pageGeometry.x : 0
pageGeometry.y : 0
dispose : Undefined
iterations : 0
compression : JPEG
quality : 85
orientation : Undefined
properties.icc:copyright : Copyright Apple Inc., 2020
properties.icc:description : Display
properties.jpeg:colorspace : 2
properties.jpeg:sampling-factor : 2x2,1x1,1x1
properties.signature : 3e5eb35a1ed3210c743fa28192c08f5f7848895f2d0568bcfaaadcc1326d88eb
profiles.icc :
tainted :
filesize : 80714
numberPixels : 723600
filename : d2ab531a0a64fa874c3a429e5194655269f8fb622711ed83745bea487aae38ce.jpg
name : d2ab531a0a64fa874c3a429e5194655269f8fb622711ed83745bea487aae38ce.jpg
format : JPEG
formatDescription : Joint Photographic Experts Group JFIF format
mimeType : image/jpeg
class : DirectClass
geometry.width : 603
geometry.height : 1200
geometry.x : 0
geometry.y : 0
units : Undefined
type : TrueColor
endianess : Undefined
colorspace : sRGB
depth : 8
baseDepth : 8
channelDepth.red : 8
channelDepth.green : 8
channelDepth.blue : 8
pixels : 723600
renderingIntent : Perceptual
gamma : 0.454545
backgroundColor : #FFFFFF
borderColor : #DFDFDF
matteColor : #BDBDBD
transparentColor : #000000
interlace : JPEG
intensity : Undefined
compose : Over
pageGeometry.width : 603
pageGeometry.height : 1200
pageGeometry.x : 0
pageGeometry.y : 0
dispose : Undefined
iterations : 0
compression : JPEG
quality : 85
orientation : Undefined
properties.icc:copyright : Copyright Apple Inc., 2020
properties.icc:description : Display
properties.jpeg:colorspace : 2
properties.jpeg:sampling-factor : 2x2,1x1,1x1
properties.signature : 3e5eb35a1ed3210c743fa28192c08f5f7848895f2d0568bcfaaadcc1326d88eb
profiles.icc :
tainted :
filesize : 80714
numberPixels : 723600
filename : d2ab531a0a64fa874c3a429e5194655269f8fb622711ed83745bea487aae38ce.jpg
Image Search Tags:
Many thousands of MSDNC direct attacks have failed to control the reach [sway opinion] and prevent growth ['free-thought'].
When direct attacks [use of inserts [cutouts]] fail > censorship [ban] deployed as aggressive method to slow/limit growth.
Next: more 'act of violence' frame-ups
CONTROLLED INFORMATION DISSEMINATION SYSTEM DESIGNED TO CONTROL YOU IS THREATENED.
If you posed no threat [reach and topics] to their control [information dominance] they would not continue to expend ammunition.
They would not care.
#2 attacked topic [#1 POTUS].
ALL FOR A 'CONSPIRACY'.
INFORMATION WARFARE.
INFILTRATION NOT INVASION.
Q
When direct attacks [use of inserts [cutouts]] fail > censorship [ban] deployed as aggressive method to slow/limit growth.
Next: more 'act of violence' frame-ups
CONTROLLED INFORMATION DISSEMINATION SYSTEM DESIGNED TO CONTROL YOU IS THREATENED.
If you posed no threat [reach and topics] to their control [information dominance] they would not continue to expend ammunition.
They would not care.
#2 attacked topic [#1 POTUS].
ALL FOR A 'CONSPIRACY'.
INFORMATION WARFARE.
INFILTRATION NOT INVASION.
Q
Display Options
Delta to next: 0 D_00:36:17 (seconds total: 2177) (17) (8)
Q !!Hs1Jq13jV6 07/22/2020 12:08:37 ID: c8fd87
8kun/qresearch: 10044656Q Clock [ Min: 58 | :25/:55 Mir: 52 | 180 Mir: 28 | :35/:05 Mir: 12 ]
Image Name: EdfmkT7XoAUOgjO.jpg
Filename: c8330bd61a307ce0f41f6caa285a10ad41b5aa06fa13b2d0f9fed56054a18905.jpg
EXIF DATA
name : c8330bd61a307ce0f41f6caa285a10ad41b5aa06fa13b2d0f9fed56054a18905.jpg
format : JPEG
formatDescription : Joint Photographic Experts Group JFIF format
mimeType : image/jpeg
class : DirectClass
geometry.width : 828
geometry.height : 1552
geometry.x : 0
geometry.y : 0
resolution.x : 72
resolution.y : 72
printSize.x : 11.5
printSize.y : 21.5556
units : Undefined
type : TrueColor
endianess : Undefined
colorspace : sRGB
depth : 8
baseDepth : 8
channelDepth.red : 8
channelDepth.green : 8
channelDepth.blue : 8
pixels : 1285056
renderingIntent : Perceptual
gamma : 0.454545
backgroundColor : #FFFFFF
borderColor : #DFDFDF
matteColor : #BDBDBD
transparentColor : #000000
interlace : JPEG
intensity : Undefined
compose : Over
pageGeometry.width : 828
pageGeometry.height : 1552
pageGeometry.x : 0
pageGeometry.y : 0
dispose : Undefined
iterations : 0
compression : JPEG
quality : 85
orientation : Undefined
properties.icc:copyright : Copyright Apple Inc., 2017
properties.icc:description : Display P3
properties.jpeg:colorspace : 2
properties.jpeg:sampling-factor : 2x2,1x1,1x1
properties.signature : 107fd1670af6a60e1572948eb209dcb1f8636f375946d38aec493a0eacf687a4
profiles.icc :
tainted :
filesize : 163116
numberPixels : 1.28506M
filename : c8330bd61a307ce0f41f6caa285a10ad41b5aa06fa13b2d0f9fed56054a18905.jpg
name : c8330bd61a307ce0f41f6caa285a10ad41b5aa06fa13b2d0f9fed56054a18905.jpg
format : JPEG
formatDescription : Joint Photographic Experts Group JFIF format
mimeType : image/jpeg
class : DirectClass
geometry.width : 828
geometry.height : 1552
geometry.x : 0
geometry.y : 0
resolution.x : 72
resolution.y : 72
printSize.x : 11.5
printSize.y : 21.5556
units : Undefined
type : TrueColor
endianess : Undefined
colorspace : sRGB
depth : 8
baseDepth : 8
channelDepth.red : 8
channelDepth.green : 8
channelDepth.blue : 8
pixels : 1285056
renderingIntent : Perceptual
gamma : 0.454545
backgroundColor : #FFFFFF
borderColor : #DFDFDF
matteColor : #BDBDBD
transparentColor : #000000
interlace : JPEG
intensity : Undefined
compose : Over
pageGeometry.width : 828
pageGeometry.height : 1552
pageGeometry.x : 0
pageGeometry.y : 0
dispose : Undefined
iterations : 0
compression : JPEG
quality : 85
orientation : Undefined
properties.icc:copyright : Copyright Apple Inc., 2017
properties.icc:description : Display P3
properties.jpeg:colorspace : 2
properties.jpeg:sampling-factor : 2x2,1x1,1x1
properties.signature : 107fd1670af6a60e1572948eb209dcb1f8636f375946d38aec493a0eacf687a4
profiles.icc :
tainted :
filesize : 163116
numberPixels : 1.28506M
filename : c8330bd61a307ce0f41f6caa285a10ad41b5aa06fa13b2d0f9fed56054a18905.jpg
Image Search Tags:
INFORMATION WARFARE.
Q
Q
Display Options
Delta to next: 2 D_11:58:36 (seconds total: 215916) (24) (6)
Q !!Hs1Jq13jV6 07/20/2020 00:10:01 ID: 14fba8
8kun/qresearch: 10017824Q Clock [ Min: 56 | :25/:55 Mir: 54 | 180 Mir: 26 | :35/:05 Mir: 14 ]
Delta to Reply: 0 D_00:14:33 (seconds total: 873) (18) (9)
Epoch: 1595217328 (43) (7)
Anonymous 07/19/2020 23:55:28 ID:311b3a 8kun/qresearch: 10017535
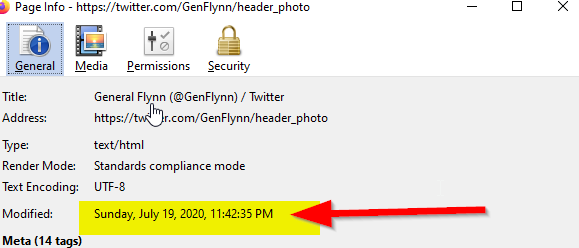
Image Name: ClipboardImage.png
Filename: 885bdbb12f7c4df757119ca54de9ab3b59913686053292164349bc5ed7d8ba4a.png
EXIF DATA
name : 885bdbb12f7c4df757119ca54de9ab3b59913686053292164349bc5ed7d8ba4a.png
format : PNG
formatDescription : Portable Network Graphics
mimeType : image/png
class : DirectClass
geometry.width : 579
geometry.height : 248
geometry.x : 0
geometry.y : 0
units : Undefined
type : TrueColorAlpha
endianess : Undefined
colorspace : sRGB
depth : 8
baseDepth : 8
channelDepth.alpha : 1
channelDepth.red : 8
channelDepth.green : 8
channelDepth.blue : 8
pixels : 143592
renderingIntent : Perceptual
gamma : 0.454545
backgroundColor : #FFFFFFFF
borderColor : #DFDFDFFF
matteColor : #BDBDBDFF
transparentColor : #00000000
interlace : None
intensity : Undefined
compose : Over
pageGeometry.width : 579
pageGeometry.height : 248
pageGeometry.x : 0
pageGeometry.y : 0
dispose : Undefined
iterations : 0
compression : Zip
orientation : Undefined
properties.png:IHDR.bit-depth-orig : 8
properties.png:IHDR.bit_depth : 8
properties.png:IHDR.color-type-orig : 6
properties.png:IHDR.color_type : 6 (RGBA)
properties.png:IHDR.interlace_method : 0 (Not interlaced)
properties.png:IHDR.width,height : 579, 248
properties.png:sRGB : intent=0 (Perceptual Intent)
properties.signature : bb2443f8c214ea6c1afa49cbeba16ecc2fbfeafedf716e522902cfb2107446ce
tainted :
filesize : 20128
numberPixels : 143592
filename : 885bdbb12f7c4df757119ca54de9ab3b59913686053292164349bc5ed7d8ba4a.png
name : 885bdbb12f7c4df757119ca54de9ab3b59913686053292164349bc5ed7d8ba4a.png
format : PNG
formatDescription : Portable Network Graphics
mimeType : image/png
class : DirectClass
geometry.width : 579
geometry.height : 248
geometry.x : 0
geometry.y : 0
units : Undefined
type : TrueColorAlpha
endianess : Undefined
colorspace : sRGB
depth : 8
baseDepth : 8
channelDepth.alpha : 1
channelDepth.red : 8
channelDepth.green : 8
channelDepth.blue : 8
pixels : 143592
renderingIntent : Perceptual
gamma : 0.454545
backgroundColor : #FFFFFFFF
borderColor : #DFDFDFFF
matteColor : #BDBDBDFF
transparentColor : #00000000
interlace : None
intensity : Undefined
compose : Over
pageGeometry.width : 579
pageGeometry.height : 248
pageGeometry.x : 0
pageGeometry.y : 0
dispose : Undefined
iterations : 0
compression : Zip
orientation : Undefined
properties.png:IHDR.bit-depth-orig : 8
properties.png:IHDR.bit_depth : 8
properties.png:IHDR.color-type-orig : 6
properties.png:IHDR.color_type : 6 (RGBA)
properties.png:IHDR.interlace_method : 0 (Not interlaced)
properties.png:IHDR.width,height : 579, 248
properties.png:sRGB : intent=0 (Perceptual Intent)
properties.signature : bb2443f8c214ea6c1afa49cbeba16ecc2fbfeafedf716e522902cfb2107446ce
tainted :
filesize : 20128
numberPixels : 143592
filename : 885bdbb12f7c4df757119ca54de9ab3b59913686053292164349bc5ed7d8ba4a.png
Flynn uploads his header at 11:42 PM EST 7/19/20

Image Name: EdVzrxWWAAA_EVl.jpg
Filename: 849f5ba85df3d1240b5fae19eac6d5b250c8aedc452d1a19e619f10c6ee2405b.jpg
EXIF DATA
name : 849f5ba85df3d1240b5fae19eac6d5b250c8aedc452d1a19e619f10c6ee2405b.jpg
format : JPEG
formatDescription : Joint Photographic Experts Group JFIF format
mimeType : image/jpeg
class : DirectClass
geometry.width : 565
geometry.height : 516
geometry.x : 0
geometry.y : 0
units : Undefined
type : TrueColor
endianess : Undefined
colorspace : sRGB
depth : 8
baseDepth : 8
channelDepth.red : 8
channelDepth.green : 8
channelDepth.blue : 8
pixels : 291540
renderingIntent : Perceptual
gamma : 0.454545
backgroundColor : #FFFFFF
borderColor : #DFDFDF
matteColor : #BDBDBD
transparentColor : #000000
interlace : JPEG
intensity : Undefined
compose : Over
pageGeometry.width : 565
pageGeometry.height : 516
pageGeometry.x : 0
pageGeometry.y : 0
dispose : Undefined
iterations : 0
compression : JPEG
quality : 85
orientation : Undefined
properties.jpeg:colorspace : 2
properties.jpeg:sampling-factor : 2x2,1x1,1x1
properties.signature : 8ef10af33530dccedba7bd843748fa8b3ae92043afefc251b17ca7674f64f14a
tainted :
filesize : 54110
numberPixels : 291540
filename : 849f5ba85df3d1240b5fae19eac6d5b250c8aedc452d1a19e619f10c6ee2405b.jpg
name : 849f5ba85df3d1240b5fae19eac6d5b250c8aedc452d1a19e619f10c6ee2405b.jpg
format : JPEG
formatDescription : Joint Photographic Experts Group JFIF format
mimeType : image/jpeg
class : DirectClass
geometry.width : 565
geometry.height : 516
geometry.x : 0
geometry.y : 0
units : Undefined
type : TrueColor
endianess : Undefined
colorspace : sRGB
depth : 8
baseDepth : 8
channelDepth.red : 8
channelDepth.green : 8
channelDepth.blue : 8
pixels : 291540
renderingIntent : Perceptual
gamma : 0.454545
backgroundColor : #FFFFFF
borderColor : #DFDFDF
matteColor : #BDBDBD
transparentColor : #000000
interlace : JPEG
intensity : Undefined
compose : Over
pageGeometry.width : 565
pageGeometry.height : 516
pageGeometry.x : 0
pageGeometry.y : 0
dispose : Undefined
iterations : 0
compression : JPEG
quality : 85
orientation : Undefined
properties.jpeg:colorspace : 2
properties.jpeg:sampling-factor : 2x2,1x1,1x1
properties.signature : 8ef10af33530dccedba7bd843748fa8b3ae92043afefc251b17ca7674f64f14a
tainted :
filesize : 54110
numberPixels : 291540
filename : 849f5ba85df3d1240b5fae19eac6d5b250c8aedc452d1a19e619f10c6ee2405b.jpg
Image Search Tags:
>>10017535
Display Options
Delta to next: 0 D_00:30:00 (seconds total: 1800) (9) (9)
Q !!Hs1Jq13jV6 07/19/2020 23:40:01 ID: 14fba8
8kun/qresearch: 10017199Q Clock [ Min: 55 | :25/:55 Mir: 55 | 180 Mir: 25 | :35/:05 Mir: 15 ]
https://twitter.com/PatriotDancing/status/1285054662375170049
Anons take note.
You have a rival.
Q
Anons take note.
You have a rival.
Q
Display Options
Delta to next: 0 D_00:15:05 (seconds total: 905) (14) (5)
Q !!Hs1Jq13jV6 07/19/2020 23:24:56 ID: b4fff0
8kun/qresearch: 10016912Q Clock [ Min: 55 | :25/:55 Mir: 55 | 180 Mir: 25 | :35/:05 Mir: 15 ]
Acknowledged.
God Bless America.
Q
God Bless America.
Q